Page 61 - 卫星导航2021年第1-2合期
P. 61
Chen et al. Satell Navig (2021) 2:12 Page 6 of 7
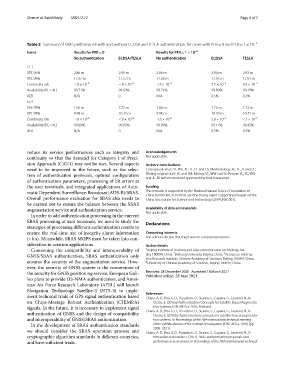
Table 2 Summary of SBAS performance with and without ECDSA and TESLA authentication, for cases with PER = 0 and PER = 1 × 10 –3
Items Results for PER = 0 Results for PER = 1 × 10 –3
No authentication ECDSA/TESLA No authentication ECDSA TESLA
L1-I
VPE 95% 2.86 m 2.90 m 2.86 m 2.94 m 2.93 m
VPL 99% 17.37 m 17.57 m 17.38 m 17.93 m 17.91 m
Continuity risk < 8 × 10 –6 < 8 × 10 –6 < 8 × 10 –6 7.7 × 10 –3 5.9 × 10 –3
Availability (PL < AL) 99.71% 99.63% 99.71% 99.80% 99.19%
AER N/A 0 N/A 0.5% 0.3%
L5-I
VPE 95% 1.66 m 1.72 m 1.66 m 1.72 m 1.72 m
VPL 99% 9.98 m 10.33 m 9.98 m 10.39 m 10.43 m
Continuity risk < 8 × 10 –6 < 8 × 10 –6 < 8 × 10 –6 5.8 × 10 –3 7.1 × 10 –3
Availability (PL < AL) 99.89% 99.85% 99.89% 99.17% 99.45%
AER N/A 0 N/A 0.5% 0.3%
reduce its service performances such as integrity and Acknowledgements
continuity so that the demand for Category I of Preci- Not applicable.
sion Approach (CAT-I) may not be met. Several aspects Authors’ contributions
need to be improved in the future, such as the selec- Conceptualization: YL, WG, XC, TL, CL and GS; Methodology: XC, TL, JL and CL;
tion of authentication protocols, optimal confguration Writing original draft: XC and SM; Editing: XC, WW and YL; Review: YL, XC, WG
of authentication parameters, processing of bit errors at and JL. All authors read and approved the fnal manuscript.
the user terminals, and integrated applications of Auto- Funding
matic Dependent Surveillance-Broadcast (ADS-B)/SBAS. This research is supported by the National Natural Science Foundation of
Overall performance evaluation for SBAS also needs to China (61601009, 41974041) and the Young Talent Supporting Program of the
China Association for Science and Technology (2019QNRC001).
be carried out to ensure the balance between the SBAS
augmentation service and authentication service. Availability of data and materials
In order to add authentication processing in the current Not applicable.
SBAS processing at user terminals, we need to study the Declarations
strategies of processing diferent authentication results to
ensure the real-time use of integrity alarm information Competing interests
(< 6 s). Meanwhile, SBAS MOPS must be taken into con- The authors declare that they have no competing interests.
sideration in aviation applications. Author details
Concerning the compatibility and interoperability of 1 Beijing Institute of Tracking and Telecommunication Technology, Bei-
3
2
GNSS/SBAS authentication, SBAS authentication only jing 100094, China. Beihang University, Beijing, China. Aerospace Informa-
ensures the security of the augmentation service. How- tion Research Institute, Chinese Academy of Sciences, Beijing 100094, China.
4
University of Chinese Academy of Sciences, Beijing 100049, China.
ever, the security of GNSS system is the cornerstone of
the security for GNSS positioning service. European Gali- Received: 28 December 2020 Accepted: 18 March 2021
leo plans to provide OS-NMA authentication, and Amer-
ican Air Force Research Laboratory (AFRL) will launch
Navigation Technology Satellite-3 (NTS-3) to imple-
ment technical trials of GPS signal authentication based References
Chiara, A. D., Broi, G. D., Pozzobon, O., Sturaro, S., Caparra, G., Laurenti, N., &
on Chips-Message Robust Authentication (CHIMRA) Chatre, E. (2016a) Authentication Concepts for Satellite-Based Augmenta-
signals. In the future, it is necessary to implement signal tion Systems, ION GNSS+ 2016, Portland.
authentication of GNSS and the design of compatibility Chiara, A. D., Broi, G. D., Pozzobon, O., Sturaro, S., Caparra, G., Laurenti, N., &
Chatre, E. (2016b). Authentication concepts for satellite-based augmenta-
and interoperability of GNSS/SBAS authentication. tion systems. In Proceedings of the 29th international technical meeting
In the development of SBAS authentication standards of the satellite division of the institute of navigation (ION GNSS+ 2016) (pp.
3208–3221).
we should consider the SBAS operation process and Chiara, A. D., Broi, G. D., Pozzobon, O., Sturaro, S., Caparra, G., Laurenti, N., &
cryptographic algorithm standards in diferent countries, Fernandez-Hernandez, I. (2017). SBAS authentication proposals and
and have sufcient trials. performance assessment. In Proceedings of the 30th international technical